|
P700
LOADING...
#ChatLiner: How To Protect Blockchain Data From Unauthorized Access
#How to protect blockchain data from unauthorized access
Just as we need to know how to access blockchain data, we also need to know how to protect it from unauthorized access.
Even when it comes to data that does not require anonymity, it is necessary to disable changes to the files and preserve the authenticity of the integrated content.
This is, for example, what it takes to create and mint authentic digital assets (ADAs) or non-fungible tokens (NFTs).
It is necessary to introduce software that embeds and cryptographically "locks" blockchain data within a file.
This software must also be able to "unlock" the file and retrieve the data embedded within it.
Both data embedding and data retrieval can only be performed using valid security tokens and cryptographic key pairs.
Otherwise, if we don't use the appropriate software, it's like guarding a house that we can't lock (because we don't have the key).
We would have to install video surveillance, build multi-layered armored doors, hire security consisting of several tens, hundreds, thousands of guards...
In the digital world, the "gatekeepers" would be computers connected to a shared network.
The ChatLiner app allows authentic digital assets to be tokenized and securely hosted on a custom blockchain network.
As a high-performance technology solution, blockchain is a safe haven for storing and sharing sensitive information and other data that requires authentication.
#Recommended articles
>> Introduction To Blockchain Technology
>> Digital Chip Card Technology (DCCT)
>> Send Digital Telegrams Over The Blockchain Network
>> Smart Contracts
>> What is tokenization in blockchain?
#Simplicity is the Virtue
With all of the above, it remains unclear why blockchain technology relies heavily on this second, far worse solution.
Instead of using a single, simple application to store, secure, and authenticate data, files, and information, most blockchain networks are based on the principle of "the more complex, the more expensive, the better".
Higher prices, however, are no guarantee of success, while complexity rarely improves quality.
The complexity of the algorithms used in blockchain technology is not a reflection of the mathematical functions underlying these algorithms.
On the contrary - it's a fairly simple formula of computing/validating hash values of all transactions in the blockchain, and most developers are familiar with it (a cryptographic hash represents an encrypted fixed-length value that identifies a given amount of data).
Complexity arises as a consequence of overexploitation of these calculations.
Due to the lack of a suitable software solution, the path of least resistance is chosen and inadequate substitutes are insisted upon.
As a result, the effectiveness of algorithms is drastically reduced due to the fact that they are unnecessarily burdened with numerous, still unsolved issues (as mentioned in the first chapter).
It is incomprehensible that some engineers persist in trying to force a solution within one and the same working environment, even though it is crystal clear that a disparate concept must be applied instead.
#ChatLiner presents the streamlined blockchain platform with end-to-end encryption
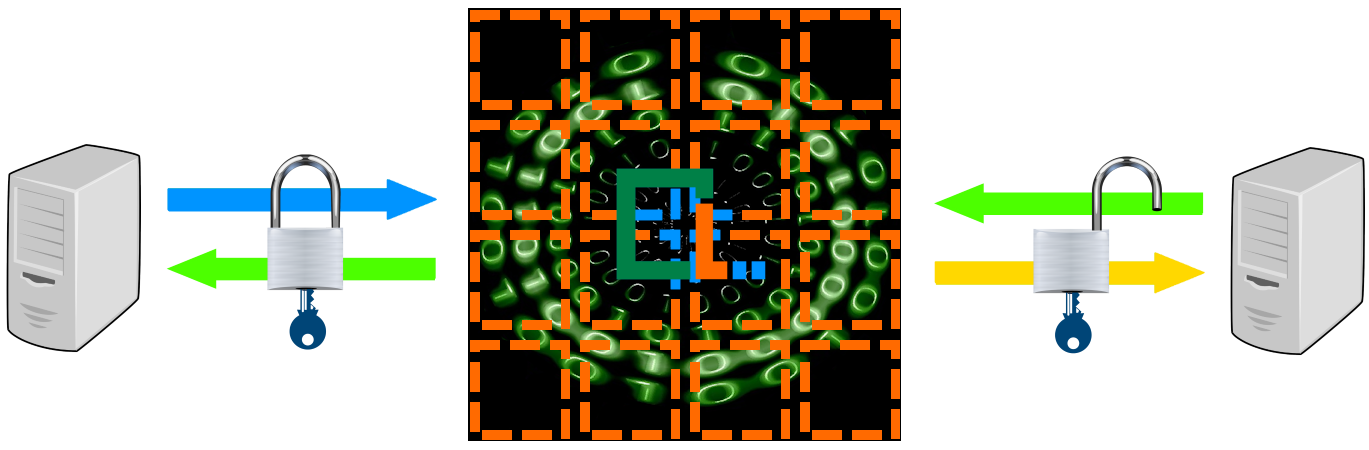
#DCCT Network is a blockchain system with up to three devices connected to a common peer-to-peer (P2P) computer network.
Designed to host authentic digital assets, it is able to verify data in a way that is completely free from external scrutiny or influence.
Transactions over the network are carried out by exchanging electronic messages in the form of digital telegrams.
|