|
P150
LOADING...
#Get Introduced To DCCL: Pave The Way For Digital Chip Card Technology Solutions
#What is Digital Chip Card Locker?
Digital Chip Card Locker, or DCCL for short, is a group of mathematically based algorithms that set the highest standards for online data protection.
It is represented by innovative solutions implemented in security protocols and e-business systems that gravitate towards preserving privacy, confidentiality, authenticity and integrity of data and protection against misuse.
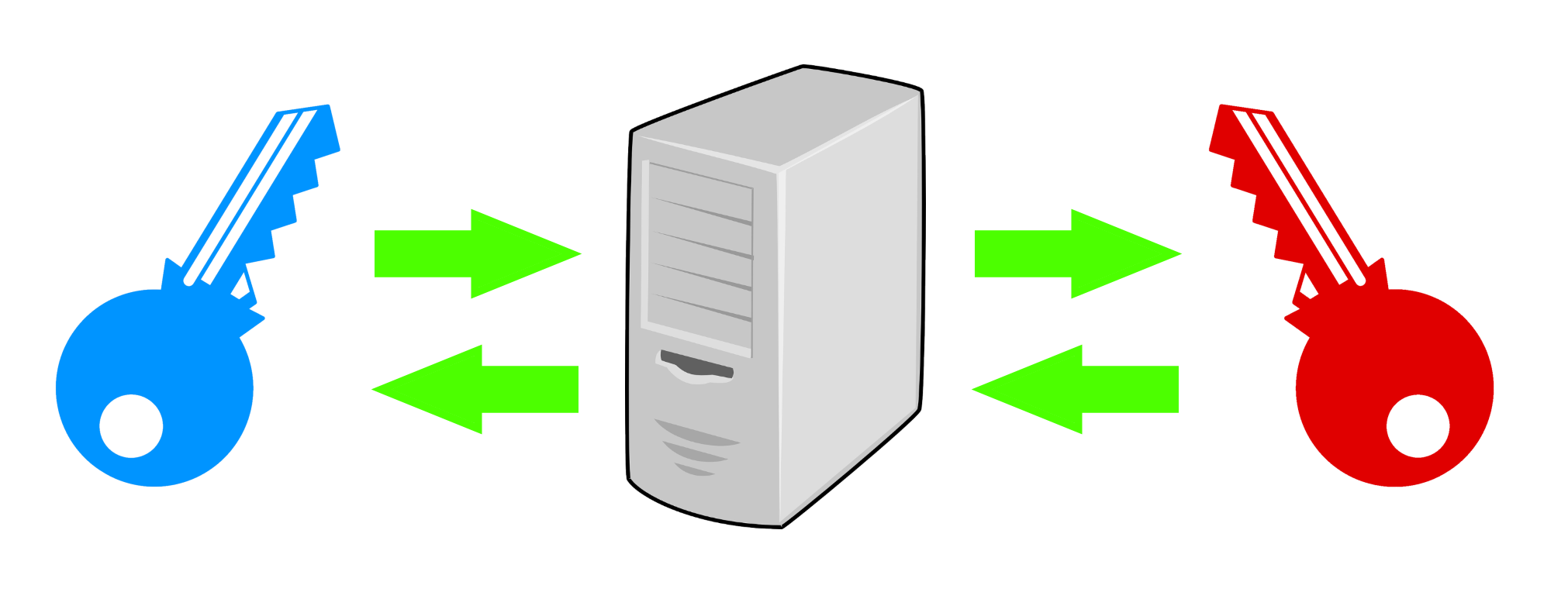
#DCCL technology structure
Digital Chip Card Locker utilizes digital signing, tokenization, and end-to-end encryption to ensure the security of data shared between users and stored on a remote database server.
End-to-end encryption is the essential part of DCCL technology implementation, while digital signatures and tokenization are its indispensable supporting elements.
#What is the flywheel of DCCL?
At the heart of DCCL lies a digital chip card, up to 1 MB in size, with an integrated virtual chip.
The "processor" of the virtual chip is powered by artificial intelligence (AI), while the "memory units" are occupied by files, associated metadata, security tags and information carriers.
#AI for the future of communications
Each virtual chip card contains metadata related to the content and the content owner (name, title, description) and optionally, a file of any type (no larger than 1MB), as an integral part of the card.
Security tokens, which typically consist of a hash code, IP address, and timestamp, are responsible for verifying the authenticity and integrity of data stored on the card's internal memory.
#The risk of data manipulation is minimized
Verification of the authenticity of a file with an integrated digital chip card is autonomous and relies on the information contained in the file itself, without resorting to external links or sources.
If the authentication of a document's identity were to be carried out using data stored outside the file, there would be a serious risk of data manipulation.
Thanks to the security mechanisms of DCCL technology that intertwine and complement each other, this risk is reduced to zero.
#Where is DCCL used?
DCCL introduces systematic, well-regulated, productive, economical and cost-effective tools for those seeking to leverage blockchain technology, initiate secure wireless and online data transmissions, digitally sign and encrypt documents.
DCCL allows us to facilitate international trade, provide secure channels for the transfer of financial information, cover all aspects of copyright and intellectual property protection, increase supply chain transparency, improve healthcare services, store files on durable and reliable media out of reach of cyber attacks, and many other services.
|